This tool uses MITRE's documented Attack Techniques and associated Mitigations to provide an alternative Risk Management tool that can be conducted on Enterprise, Mobile or Industrial Control System Infrastructures. In this short explanation, the 4-stage process is described. If not required, access the Mitigate page in the navigation bar to begin.
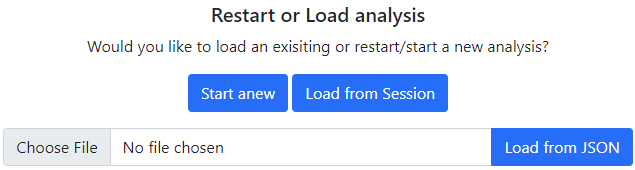
If in Stage 1 a new analysis is chosen, then a set of filters will be shown. This will initially present you with a choice of domain: Enterprise, Mobile or Industrial Control Systems. Once selected and submitted, an additional set of relevant filters are displayed.
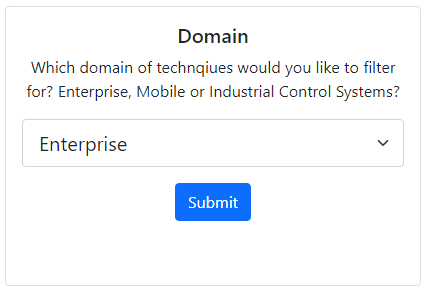
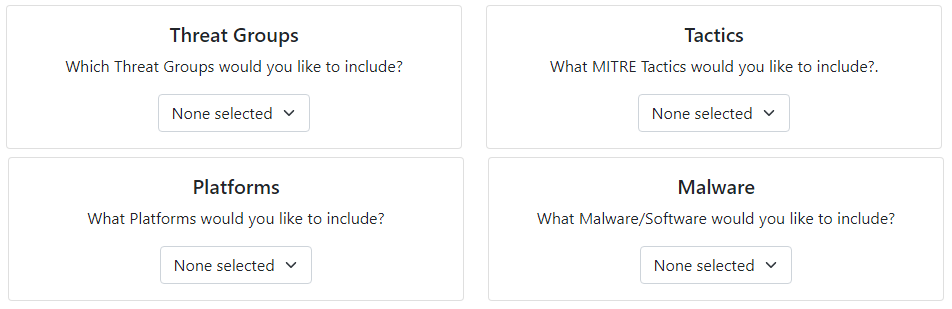
These include Threat Groups (e.g. APT-28), Mitre Tactics (MITRE ATT&CK's method to group related sets of Threats e.g. Initial Access), Platforms (e.g. Azure Active Directory, Linux), and Malware/Software (e.g. WannaCry). Please note that if you do not wish to filter by a specific area such as Tactics you must Select All the options in the dropdown list.
Below the four key filters, a few additional options can be interacted with. In the Enterprise domain, MITRE ATT&CK have offered a more granular view of a parent attack technique through sub-techniques. This can either be included or excluded from the Assessment.
Some attack techniques do not belong to specific Malware/Threat Groups and are included by default in the assessment. It is recommended that it is included to gain a wider and complete perspective of your Defensive Coverage.
The Mitigation Tolerance Level is critical to providing an analysis relevant to yourself. This defines how the overall score per technique will be calculated. For more in-depth information and additional options regarding this press the Question button.
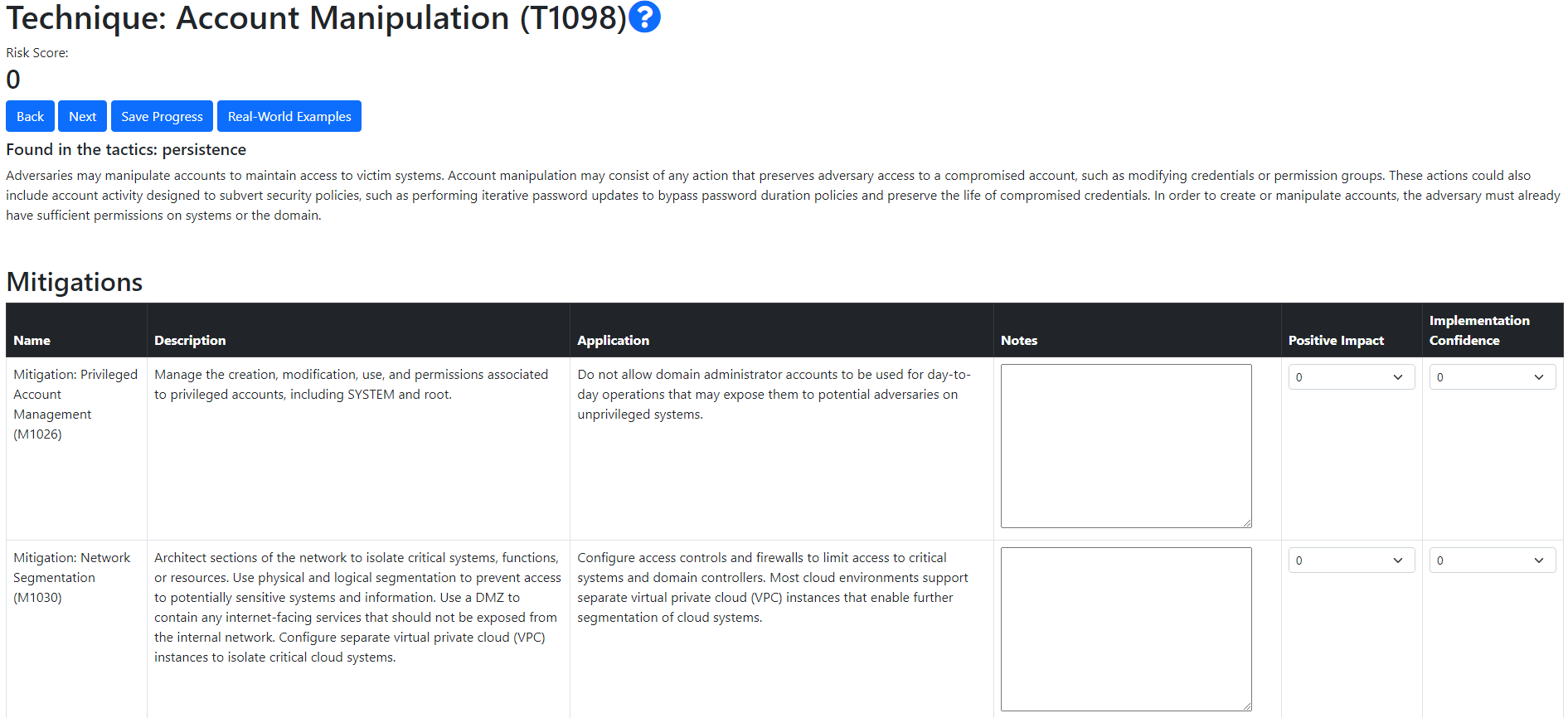
After filtering, the main assessment will now begin. You will encounter the similar style seen in the image for every Technique that has been found based on your applied filters. In the top portion,the Technique name and ID are displayed with a question mark linking to its dedicated page on MITRE ATT&CK.
Below, the Score is shown that will be updated live, reflecting inputted data into the Mitigations table. The Next and Back buttons are used to move onto different attack techniques and the Real-World Example highlights any articles that document its use in the wild. The paragraph below the `Found in tactics...` statement is a description of that attack technique.
Each row in the Mitigation table represents a single Mitigation. For each mitigation, the Risk Assessor or wider group participating in the assessment must first define a Positive Impact level. The Impact Level represents how well you believe that Mitigation will mitigate that attack technique. In the case that it flawlessly mitigates the technique a score of 10 can be assigned. The scores available are 0,2,4,6,8,10. In the case, that you believe a mitigation will have no impact a score of 0 can be assigned.
When the positive impact level is defined, the Implementation Confidence Level can now be assessed. The confidence level is used to represent your implementation of that mitigation in your infrastructure and processes; how confident are you in your implementation or are their further improvements you could make thus lowering your Confidence percentage? It is recommended to make notes throughout this process to document your reasoning.
Once defined for every Mitigation, you can now progress onto the following Technique through the Next button. If a mitigation filled in in a previous technique is present as a mitigation for another ATT&CK Technique this will be auto filled, with your previous scores and notes. If overwritten this will not overwrite your previous content of that mitigation.
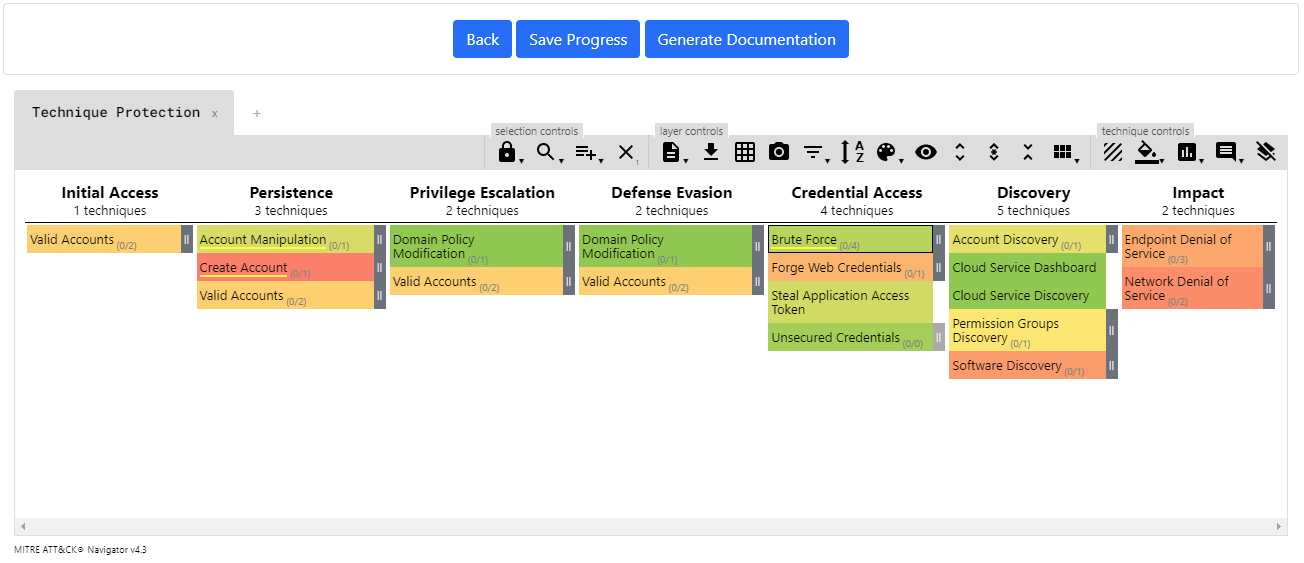
Upon analysing each Attack technique, a graphical matrix will be shown, through use of MITRE ATT&CK Navigator, and highlight potential areas of weakness in your domain. It is possible to access all your comments and view your Scores for each technique.
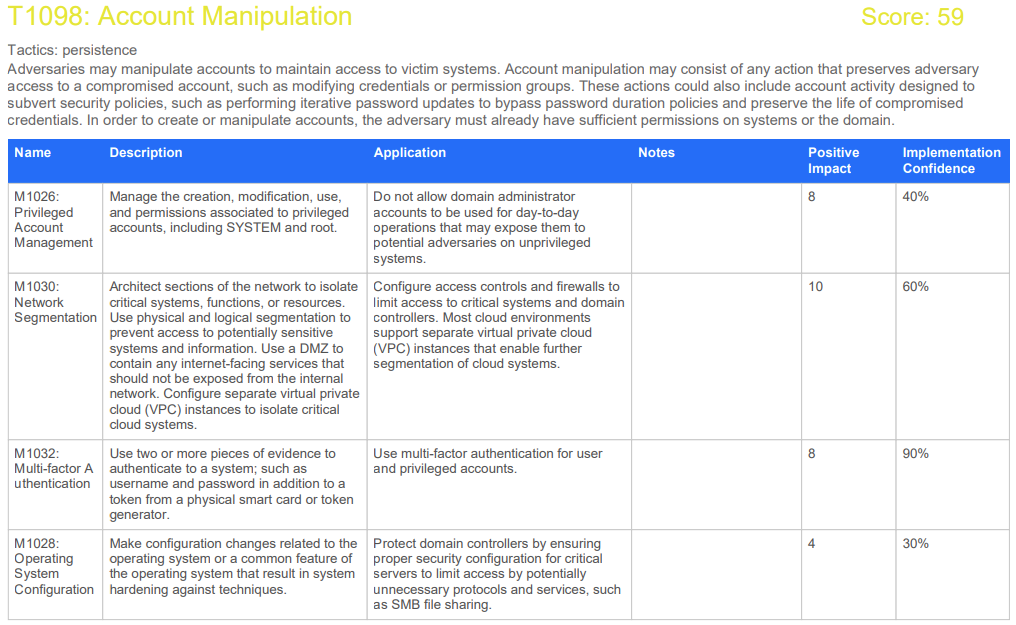
The Generate Documentation button will compile all your inputted information into a single PDF that can be used to document and outline a plan going forwards as to how your defensive posture can be improved.
©2022 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.